Wiki
SPDY
SPDY is an open networking protocol developed primarily at Google for transporting web content. SPDY manipulates HTTP traffic, with particular goals of reducing web page load latency and improving web security. SPDY achieves reduced latency through compression, multiplexing, and prioritization although this depends on a combination of network and website deployment conditions. The name "SPDY" is a trademark of Google and is not an acronym.
mod_spdy is a SPDY module for Apache 2.x that allows your web server to take advantage of SPDY features like stream multiplexing and header compression. This is the open source home for mod_spdy. You can also download Debian and RPM packages or compile mod_spdy from source.
HSTS
HTTP Strict Transport Security (HSTS) is a web security policy mechanism which is necessary to protect secure HTTPS websites against downgrade attacks, and which greatly simplifies protection against cookie hijacking. It allows web servers to declare that web browsers (or other complying user agents) should only interact with it using secure HTTPS connections, and never via the insecure HTTP protocol. HSTS is an IETF standards track protocol and is specified in RFC 6797.
External Links
Chromium SPDY www.chromium.org/spdy/spdy-whitepaper
Apache SPDY module code.google.com/p/mod-spdy
SPDY Google Developers developers.google.com/speed/spdy
SPDY runs over HTTPS, so we need an HTTPS-enabled web site to test SPDY. Please note that SPDY will fall back to HTTPS if the user's browser doesn't support SPDY or if things go wrong, so installing mod_spdy doesn't hurt your existing setup.
I'm assuming that you have a working LAMP setup, as described on Installation LAMP ( Apache+MySQL+PHP ) on Ubuntu and Set Up Apache with a Free Signed SSL Certificate on. This tutorial explains how to use mod_spdy with Apache 2.4.12 on Ubuntu 14.04 LTS.
Installing mod_spdy
Google provides Debian/Ubuntu packages for mod_spdy on https://developers.google.com/speed/spdy/mod_spdy does not yet support Ubuntu 14.04 or Apache 2.4, so I use OpenSSL 1.0.1(h) and Apache 2.4.10 port for mod-spdy.
$ cd /tmp $ sudo apt-get -y install git g++ libapr1-dev libaprutil1-dev curl patch binutils make devscripts $ git clone https://github.com/eousphoros/mod-spdy.git $ cd mod-spdy/src $ ./build_modssl_with_npn.sh $ chmod +x ./build/gyp_chromium $ make BUILDTYPE=Release $ sudo service apache2 stop $ cd /usr/lib/apache2/modules $ mv mod_ssl.so mod_ssl.so.bak $ cd /tmp/mod-spdy/src $ sudo cp mod_ssl.so /usr/lib/apache2/modules $ sudo service apache2 start $ sudo a2enmod ssl $ sudo service apache2 restart $ sudo cp out/Release/libmod_spdy.so /usr/lib/apache2/modules/mod_spdy.so $ echo "LoadModule spdy_module /usr/lib/apache2/modules/mod_spdy.so" | sudo tee /etc/apache2/mods-available/spdy.load $ echo "SpdyEnabled on" | sudo tee /etc/apache2/mods-available/spdy.conf $ sudo a2enmod spdy $ sudo service apache2 restart
Enforce HTTPS with Strict Transport Security (HSTS)
For Apache, you'll only have to indicate:
# charge the mod_headers.so module if it is not charged already LoadModule headers_module modules/mod_headers.so
or use this commands
$ sudo a2enmod headers
add the following line to your HTTPS virtual host config
<VirtualHost *:443>
# ...
# Strict-Transport-Security supporteded enforce HTTPS connections for 180 days
Header add Strict-Transport-Security: "max-age=15552000; includeSubDomains; preload"
# ...
</VirtualHost>
For nginx, do
# Strict-Transport-Security supporteded enforce HTTPS connections for 180 days add_header Strict-Transport-Security "max-age=15552000; includeSubDomains; preload";
Redirect HTTP to HTTPS
For Apache, add the following line to HTTPS virtual host config
<VirtualHost *:80>
# ...
# Force HTTPS
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteCond %{SERVER_PORT} 80
RewriteCond %{HTTPS} !=on
RewriteRule (.*) https://%{HTTP_HOST}%{REQUEST_URI}
</IfModule>
# ...
</VirtualHost>
or config in .htaccess
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteCond %{SERVER_PORT} !^443$
RewriteRule ^/(.*) https://%{HTTP_HOST}/$1 [NC,R=301,L]
</IfModule>
Now let's test if SPDY is working. We need a browser with SPDY support. This website (SPDYCheck.org) can be check if a website properly supports the SPDY protocol, the super fast HTTP replacement, and troubleshoot any problems with the configuration.
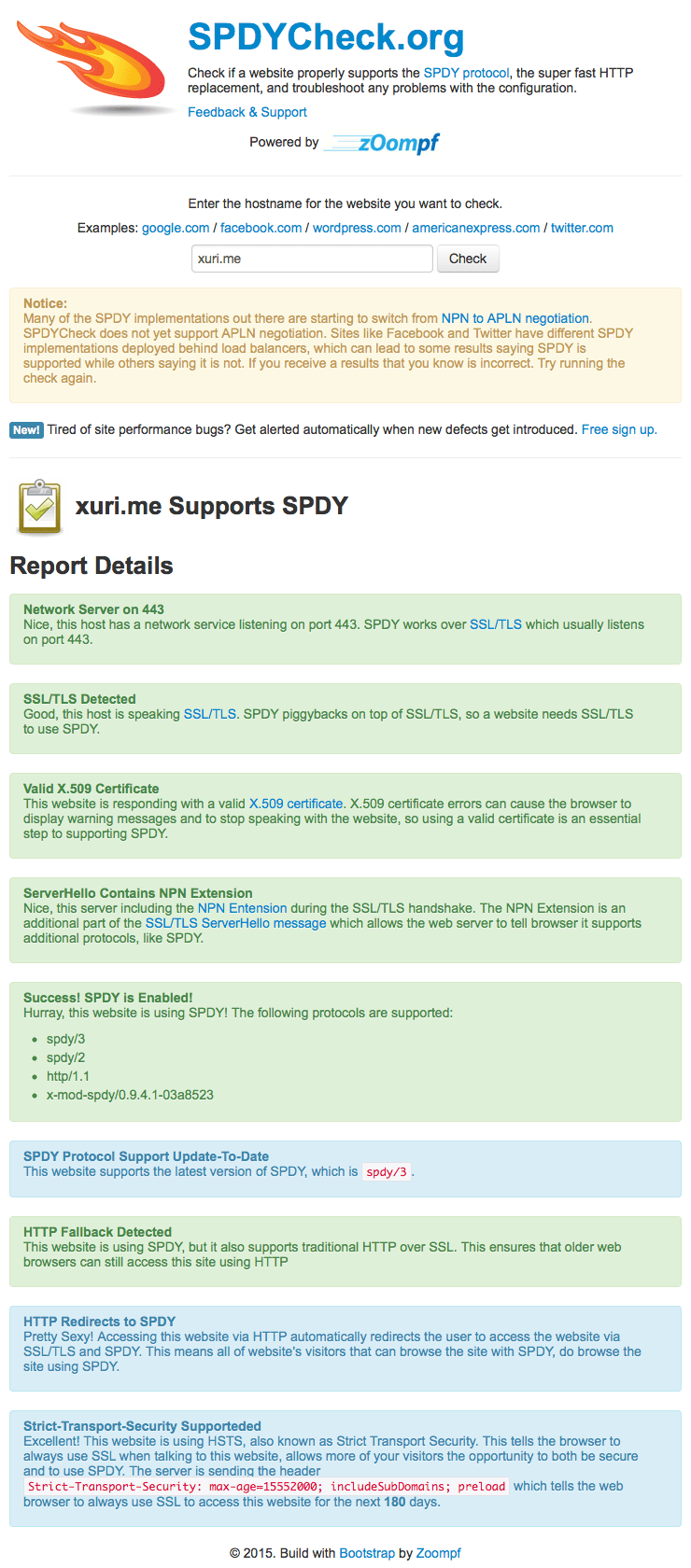
In another way, we use Google Chrome and reload the SSL web site, it is important that you reload it so that it can use SPDY (the first time you loaded it in chapter 1 it used normal HTTPS). Afterwards, open a new tab and type in the URL chrome://net-internals/#spdy, if everything went well, your SSL vhost should now be listed in the table which means SPDY support is working.
See more Enabling SPDY and HSTS on Nginx