Introduction
The certificates were used to impersonate numerous sites in Iran, such as Gmail and Facebook, which enabled the operators of the fake sites to spy on unsuspecting site users. In another case, a Malaysian subordinate certificate authority (DigiCert Sdn. Bhd.), mistakenly issued 22 weak SSL certificates, which could be used to impersonate websites and sign malicious software. As a result, major browsers had to revoke their trust in all certificates issued by DigiCert Sdn. Bhd. (Note: DigiCert Sdn. Bhd. is not affiliated with the U.S.-based corporation DigiCert, Inc.)
Get more information from Certificate Transparency official website.
Enable Certificate Transparency via TLS Extension for Nginx
TLS Extension
Server operators can deliver SCTs by using a special TLS extension (see figure 2). In this case, the CA issues the certificate to the server operator, and the server operator submits the certificate to the log. The log sends the SCT to the server operator, and the server operator uses a TLS extension with type signed_certificate_timestamp to deliver the SCT to the client during the TLS handshake.
This method does not change the way a CA issues SSL certificates. However, it does require a server change to accommodate the TLS extension.
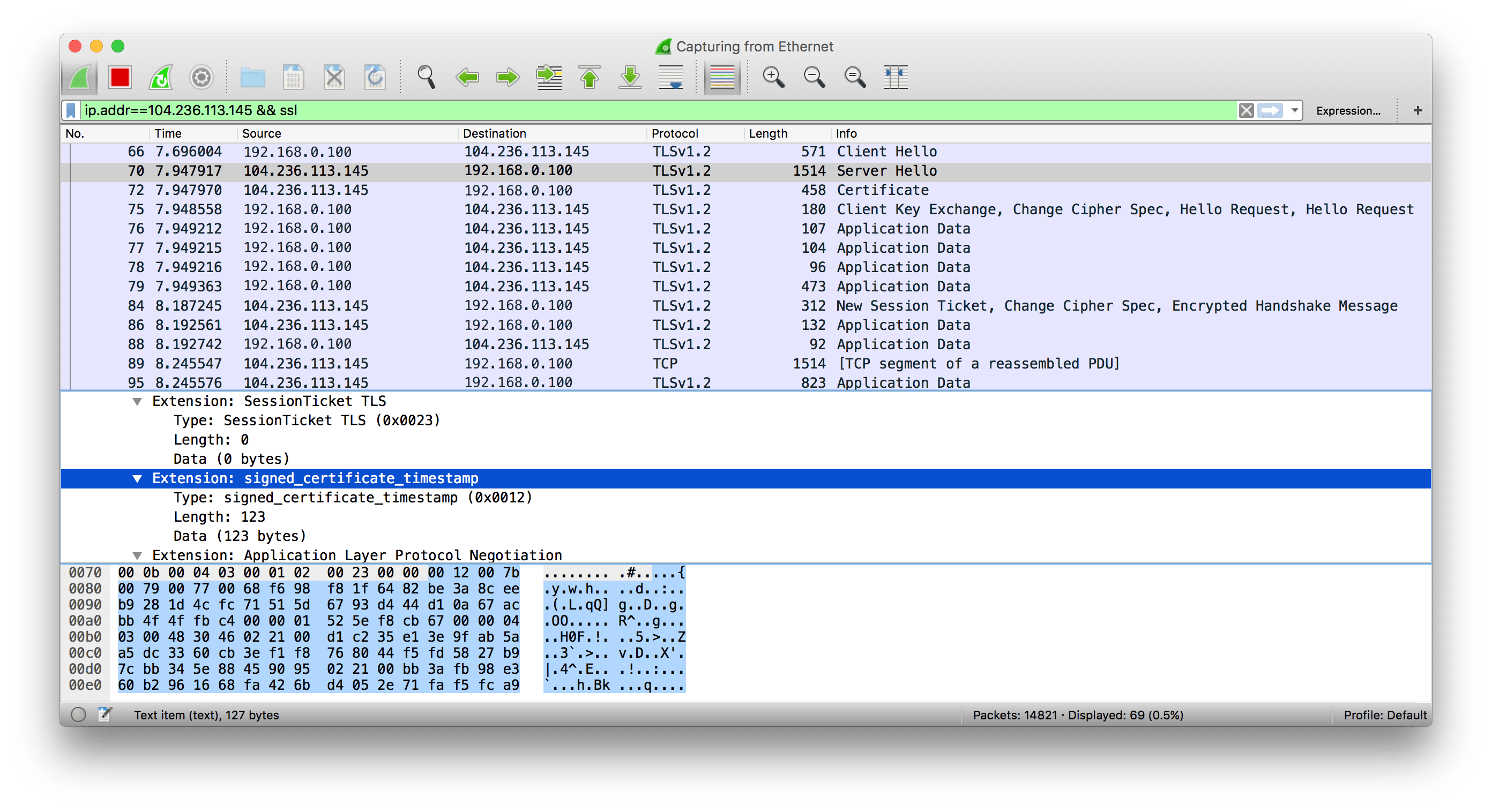
We can get signed_certificate_timestamp TLS Extension in server handshake stage Server Hello responsed via network protocol analyzer such Wireshark.
Get SCT File
ct-submit is a program that submits X.509 certificate chains to Certificate Transparency log servers. It returns the Signed Certificate Timestamp structure in a format suitable for use with Apache's mod_ssl_ct module and nginx-ct.
Install Go and ct-submit
$ sudo apt-get install golang $ wget -O ct-submit.zip -c https://github.com/grahamedgecombe/nginx-ct/archive/master.zip $ unzip ct-submit.zip $ cd ct-submit-master $ go build
Using executable file ct-submit-1.0.0 submit crt or pem format certificate file, and get a sct format file.
$ ./ct-submit-master ct.googleapis.com/aviator <~/www/ssl/chained.crt >~/www/scts/aviator.sct $ ./ct-submit-master ct1.digicert-ct.com/log <~/www/ssl/chained.crt >~/www/scts/digicert.sct
I have submit my certificate to Google and Digicert server in this example, we can find more server from Certificate Transparency Server List.
Add Certificate Transparency (CT) Module for Nginx
Config nginx-ct with OpenSSL 1.0.2+, I used CloudFlare patched OpenSSL
$ git clone https://github.com/cloudflare/sslconfig $ wget -O openssl.zip -c https://github.com/openssl/openssl/archive/master.zip $ unzip openssl.zip $ mv openssl-master/ openssl $ cd openssl && patch -p1 < ../sslconfig/patches/openssl__chacha20_poly1305_cf.patch $ cd ../ $ wget -c http://nginx.org/download/nginx-1.9.11.tar.gz $ tar zxf nginx-1.9.10.tar.gz $ wget -O nginx-ct.zip -c https://github.com/grahamedgecombe/nginx-ct/archive/master.zip $ unzip nginx-ct.zip $ ./configure \ --http-client-body-temp-path=/var/run/nginx/body \ --http-fastcgi-temp-path=/var/run/nginx/fastcgi \ --http-proxy-temp-path=/var/run/nginx/proxy \ --http-scgi-temp-path=/var/run/nginx/scgi \ --http-uwsgi-temp-path=/var/run/nginx/uwsgi \ --user=www-data \ --group=www-data \ --prefix=/etc/nginx \ --sbin-path=/usr/sbin/nginx \ --conf-path=/etc/nginx/nginx.conf \ --error-log-path=/var/log/nginx/error.log \ --http-log-path=/var/log/nginx/access.log \ --pid-path=/var/run/nginx.pid \ --lock-path=/var/run/nginx.lock \ --with-pcre-jit \ --with-ipv6 \ --with-http_v2_module \ --with-debug \ --with-http_stub_status_module \ --with-http_realip_module \ --with-http_addition_module \ --with-http_dav_module \ --with-http_gzip_static_module \ --with-http_sub_module \ --with-http_xslt_module \ --with-http_ssl_module \ --with-ld-opt=-lrt \ --add-module=../nginx-ct-master \ --with-openssl=../openssl \ --with-http_v2_module \ --with-http_ssl_module $ make $ sudo service nginx stop $ make install
Add following code in Nginx configuration file.
ssl_ct on; ssl_ct_static_scts /your/path/to/scts;
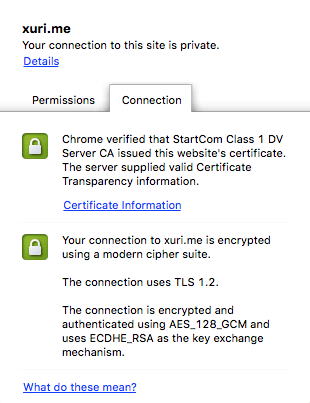
Validate Certificate Transparency on Google Chrome
Certificate without SCT information will prompt: The server did not supply any Certificate Transparency information.
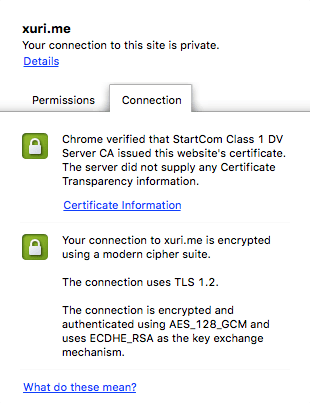
Certificate with SCT information will prompt: The server supplied valid Certificate Transparency information.